| Date | Day | Time | Duration |
| 15 May | Monday | 11:30 to 19:30 IST/GMT+5.30 | 8 Hours |
| 16 May | Tuesday | 11:30 to 19:30 IST/GMT+5.30 | 8 Hours |
Candidates will get FULL 30 Days Lab Access after training which comes with technical support.
Apex Threat Actors having advanced capabilities like leveraging in-memory implants, writing custom codes to evade AVs & EDR, moving laterally with custom made Tools, evading host and network level security solutions with covertness etc are constantly consolidating their attack techniques (and Tactics)
against Defensive Teams. To strengthen the enterprise grade security, the training is designed for penetration testers, system administrators and Blue Team members to understand different tactics, techniques and attacks used by adversaries.
Students will gain enough knowledge of the enterprise-grade security controls and how they can be stealthily evaded in Host-level, Network-level and Active Directory network. Class will go through the threat actors TTPs, writing custom scripts in C# & abusing Windows API for evading host & network controls to
abusing restrictions in Active Directory Environment of Windows & Linux platforms in order to better refine detection in an enterprise.
– Mythic C2
– Domain Setup
– Redirector Setup
– Cloud Premise
– On-Premises
– Payload Server
– Operational Security (OPSEC)
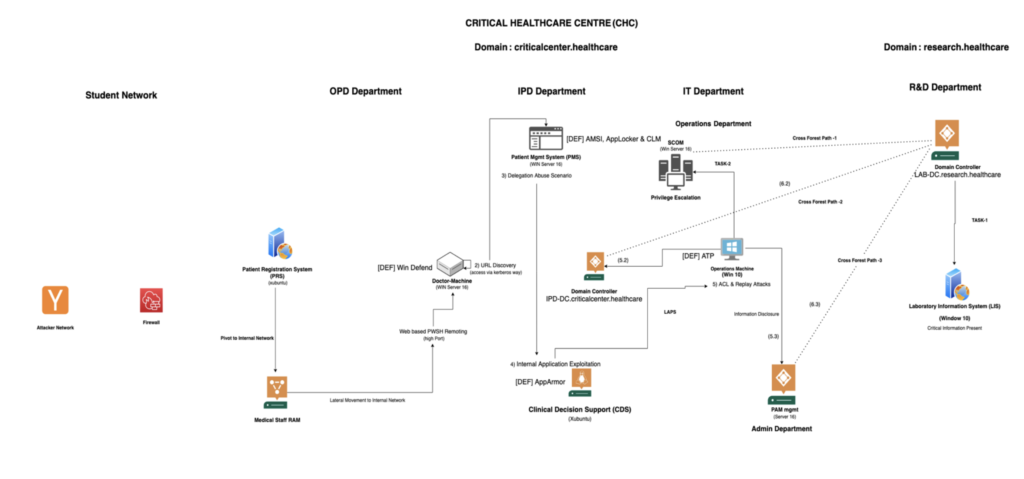
– AMSI, CLM, ASR Rules, UAC Bypass, AppLocker, Credential Guard
– Constrained Delegation & Resource based constrained delegation
– Cross Forest Abuse Scenarios [5 Different Techniques]
**Candidates will get FULL 30 Days Lab Access after training which comes with technical support.
The cyber range lab has deployment of various Host–Level, Network–Level and AD Level security controls. Enterprise grade EDRs with cloud–level protection are enabled, training will provide ways of bypassing these security controls in real–time.

Yash Bharadwaj, Co-Founder & Technical architect at CyberWarFare Labs with over 4.5 Years of Experience as Technologist. Highly attentive towards finding, learning and discovering new TTP’s used during offensive engagements.
His area of interest includes building Red / Blue team infrastructure, evading AVs & EDRs, Pwning Active Directory infrastructure, stealth enterprise networks & Multi cloud attacks. Previously he has delivered hands-on red / blue / purple team trainings / talks / workshops at Nullcon, X33fCon, NorthSec, BSIDES Chapters, OWASP, CISO Platform, YASCON. You can reach out to him on Twitter @flopyash

Manish Gupta is Director of CyberWarFare Labs having 6.5+ years of expertise in offensive Information Security. Where he specializes in Red Teaming Activities on enterprise Environment. His Research interest includes Real World Cyber Attack Simulation and Advanced persistent Threat (APT). Previously he has presented his research at reputed conferences like Blackhat USA, DEFCON, Nullcon, BSIDES Chapters, X33fcon, NorthSec & other corporate trainings etc.
